IntegriKey – keeps your input data secure
Would you consider connecting to your bank account in an internet café? Too risky? ETH researcher Aritra Dhar explains how to make sure that the message you send is the message received, even in a hostile environment.

What is the problem with using public computers for data transfer?
Users of public computers have little control over their environment. The host computer could be infected with a virus and someone could spy on the public WLAN. With IntegriKey, however, we provide a secure island in a potentially hostile environment that makes sure, that when you type the letter “A” on the keyboard, “A” will be received at the other end, e.g. your bank. No-one can mess with your input data.
How does IntegriKey work?
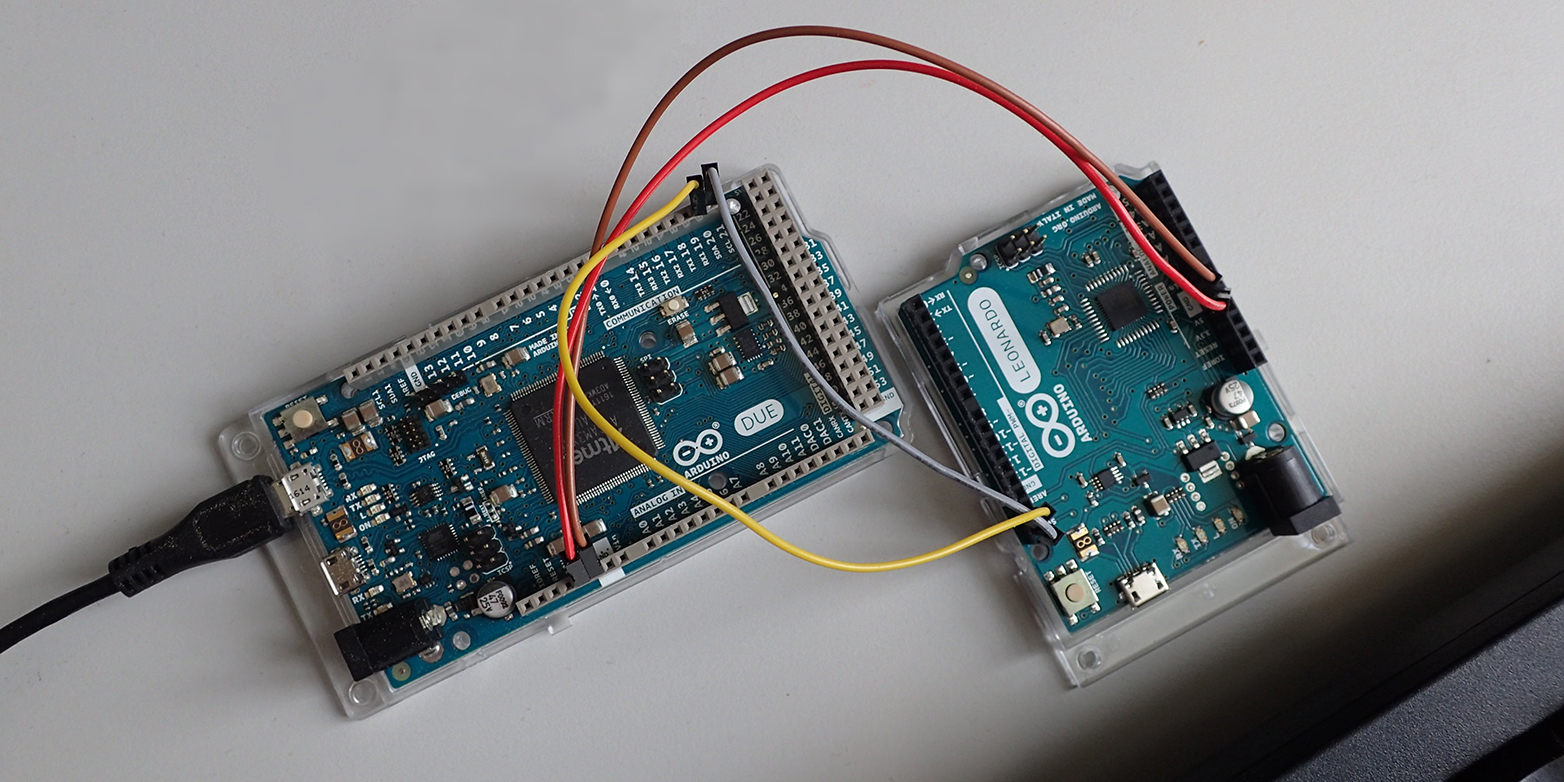
IntegriKey is an embedded device, which you plug between the keyboard and the untrusted host computer (see fig. 1). IntegriKey provides a 2-factor authenticity for input data. You may know the 2-factor authenticity from your bank, where they first ask for your username and password followed by a certification from a second device, i.e. a PIN from a mobile phone app. We follow a similar concept for IntegriKey, where IntegriKey provides the second factor.
How secure is IntegriKey?
First, IntegriKey is like a physical key that you should not hand over to anyone. It carries your client identity. You plug it in when needed and take it with you as you leave. Second, as an embedded device IntegriKey cannot be hacked. It has very few components and is programmed with less than 2’000 lines of code. There is basically nothing for a hacker to tamper with.
What are typical fields of application?
Fraud in e-banking is one example. We think, however, that IntegriKey will have an even stronger impact in areas where malicious modifications of input parameters can cause physical damage. In the production industry, for example, modifications to a process parameter could cause irreversible damage to machinery: A turbine could spin too fast or a reactor could overheat. IntegriKey can protect PLC commands that control safety critical equipment. Another example is the growing field of online medical services. Doctors want to be sure that patient data is transferred correctly. Just imagine the consequences of tampered input for a pacemaker!
IntegriKey is a new product for the enforcement of security properties in a highly adversarial environment. No such product is currently on the market. Therefore, it would be an exciting opportunity to optimize and customize IntegriKey with an industrial partner for a specific application. If you are interested, please, contact us!
Contact / Links:
System Security Group Professor Srdjan Capkun
Technology filed for a patent, Ref. 2017-147
Do you want to subscribe to ETH News for Industry?
external page Subscribe to our newsletter
Are you looking for research partners at ETH Zurich?
Contact ETH Industry Relations
